The Shared Responsibility Model: What Startups Need to Know About Cloud Security in 2025
After transferring to the cloud, many startups normally really feel all the load is lifted, and they’re lastly free from {hardware} complications. They assume main cloud suppliers like Azure, AWS, or Google Cloud maintain each side of cloud safety.
These suppliers shield issues beneath, however you might be nonetheless chargeable for the security of your information, settings, and entry guidelines. This is the place shared accountability comes in. Not understanding how this works accurately can imply hassle, like exposing your working system, functions, and information to cyber attackers.
To provide help to keep away from these failures, in this text, I’ll break down how shared accountability works and the mandatory actions you and your staff want to take to safe your cloud surroundings. If you might be already leveraging cloud computing or heading there, that is for you.
What is the Shared Responsibility Model all about?
Shared accountability is the collaborative effort between cloud suppliers and their clients. This mannequin specifies the obligations of each events in retaining the cloud surroundings secure. The cloud supplier is chargeable for safeguarding the cloud infrastructure, whereas clients are chargeable for securing what’s contained in the cloud, together with functions, configurations, and information.
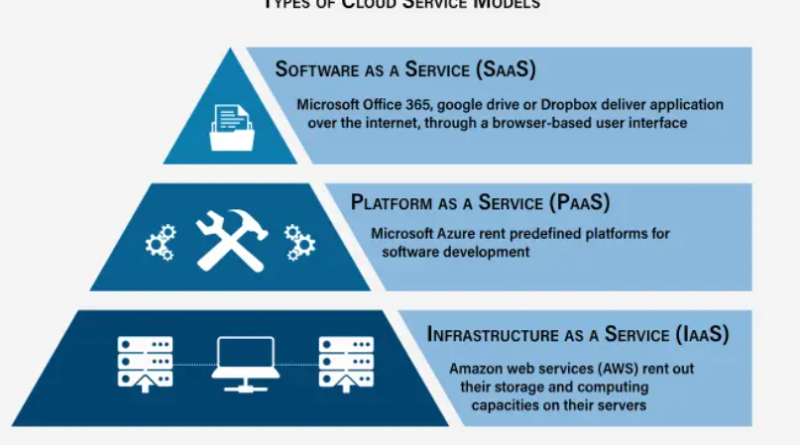
How Shared Responsibility Varies Across IaaS, PaaS, and SaaS
From a common perspective, the concept behind the shared accountability mannequin is kind of straightforward to perceive: you, the cloud buyer, safeguard sources you possibly can management in the cloud, whereas the cloud service suppliers (CSPs) take care of the remainder. However, this strategy can differ relying on the cloud service class (IaaS, PaaS, and SaaS) concerned. Let’s get proper into it and uncover how they’re completely different.
Infrastructure as a Service (IaaS): You are primarily chargeable for safety right here. The supplier offers you the mandatory instruments (server, storage), however the way you configure your setup and safe your information and app is completely up to you.
Platform as a Service (PaaS): In PaaS, the cloud suppliers do extra work. They safe the infrastructure and platform when you hold your app secure and determine who can use it.
Software as a Service (SaaS): Here, virtually every little thing, down to the software program itself, is dealt with by the CSPs. The solely factor you want to do is to management who has entry to what and guarantee customers have the right permissions.
What occurs whenever you misunderstand shared accountability?
Misunderstanding the shared accountability mannequin may result in errors that may jeopardize the safety of your cloud surroundings and enterprise. Your staff could make varied errors when they do not know their obligations. Here are frequent errors:
- Leaving S3 Buckets Public: Some startups mistakenly publicise their cloud storage (like Amazon S3). As a end result, anybody on the web can see their delicate information, similar to buyer data and firm secrets and techniques. Although exposing S3 buckets could be a easy mistake, it causes huge safety breaches. It is essential to limit entry to solely approved people.
- Using Default Passwords or Admin Access for All Users: Many startups make the error of not altering default passwords or giving all their customers admin entry to the cloud system. This is completely unsafe. Default passwords are a hacker’s dream as a result of they’re very straightforward to guess, leaving open doorways for breaches. Also, giving entry to many customers can create vulnerabilities.
- Ignoring Configuration Responsibilities: Sometimes, startups assume their suppliers have secured each side of their cloud safety and that each one safety is in place. However, this isn’t the case. You should nonetheless configure your firewalls, id entry, and encryption settings to safe your cloud surroundings.
Real penalties brought on by these frequent errors:
- An exemplary case is the Capital One breach in 2019. A misconfigured firewall working on Amazon Web Services allowed hackers to steal delicate data. This theft put the private information of greater than 100 million clients in danger, proving how a small error in safety configuration may result in a important state of affairs.
- Another key instance is the Verkada breach in 2021. Hackers managed to achieve management of a safety system that was supposed to be protected by a ‘tremendous Admin’ account, which had its username and password publicly obtainable. This account supplied hackers entry to Verkada’s AWS-hosted digicam techniques. They gained management of over 150,000 safety cameras in extraordinarily delicate areas, together with hospitals, prisons, Cloudflare workplaces, and Tesla factories. They exploited their privileged entry to view dwell and archived footage of personal areas and launched some clips.
The influence of those errors could be extreme. Startups could face:
- Data Leaks: Sensitive buyer or enterprise data is made public.
- Lawsuits: Companies could face lawsuits by shoppers or companions if their information is breached.
- Fines from Regulators: If you break the regulation on information safety, you have got to face penalties from regulators like GDPR and CCPA, which can end result in paying fines.
- Loss of Trust: Regaining the belief of consumers shall be troublesome as soon as they lose confidence in your organization’s potential to hold their information secure
What Startups Are Responsible For
As a startup, you have got a big position to play in safeguarding your cloud surroundings, and right here is how one can go about it.
1. Team schooling: Educating your workers on cloud safety will go a good distance in sustaining the security of your cloud surroundings. Make positive everyone seems to be aware of the shared accountability mannequin and the half they play in the cloud’s protection. Conduct inside safety coaching classes on dangers, entry management, and incident response to mitigate safety breaches brought on by human error.
2. Data: Encrypt your information to hold it secure from hackers and save backup copies in case one thing goes unsuitable.
3. User permissions and id entry administration (IAM): Everyone should not have full management. Follow the least privilege precept, and provides every consumer the minimal permissions mandatory to carry out their duties. It is essential to frequently audit and modify permissions as consumer roles change to keep away from overexposing delicate information and sources.
4. App-level safety: Ensure the apps you create or use are safe. Pay consideration to the APIs connecting these apps and safe them with robust authentication and encryption. Update software program frequently to patch vulnerabilities.
5. Configuring cloud sources: Setting up your cloud is your accountability. Select the appropriate permissions (similar to role-based entry) and safety settings to make sure that nothing is left susceptible to assault.
6. Monitoring and alerting: Watch out for hassle. You want to acknowledge something odd or suspicious and give you the chance to reply instantly if one thing occurs. Always have an incident response plan.
Here’s a fast guidelines you need to use to keep on monitor:
 Educate your Team.
Educate your Team.
 Encrypt information, shield it, and carry out backups.
Encrypt information, shield it, and carry out backups.
 Restrict administrative privileges and entry.
Restrict administrative privileges and entry.
 Secure your APIs and guarantee your software program is present.
Secure your APIs and guarantee your software program is present.
 Use the suitable settings for cloud instruments and techniques.
Use the suitable settings for cloud instruments and techniques.
 Monitor and configure notifications for unusual behaviour.
Monitor and configure notifications for unusual behaviour.
 Always have an incident response technique in place.
Always have an incident response technique in place.
What Cloud Providers Are Responsible For
When you utilize a cloud service, similar to Amazon Web Services (AWS) or Google Cloud, the supplier has important responsibilities- however just for sure elements. In easy phrases, here’s what they handle:
1. Physical safety: Providers hold the server working easily and safe information facilities with subtle measures like biometric entry, retaining the ability on, and 24/7 monitoring. Protecting it from catastrophe or break-ins.
2. Network infrastructure: They oversee the {hardware} (servers and storage) and the software program that retains the infrastructure working easily.
3. Host OS and hypervisor: Cloud suppliers handle the working system and the hypervisor. A hypervisor, also referred to as the Virtual Machine Monitor (VMM), allows a number of digital machines to run on a single bodily server.
4. Managed providers are safe (to an extent): If you utilize a managed database like Amazon RDS, the supplier secures the database. However, they do not handle your login data; the way you shield your passwords and credentials is up to you.
Here’s the important level you want to bear in mind: “Security of the cloud” is the accountability of the supplier; they safe their techniques. “Security in the cloud” is up to you; you have received to safe what you have got inside their system.
Other Effective Strategies for Cloud Security
You and your cloud supplier want to work collectively in your cloud safety. These greatest practices be sure that you do your half in securing your cloud surroundings.
1. Use a Zero Trust Approach
Zero Trust Security goes past perimeter-based defenses. It assumes no consumer or machine inside or past your community could be trusted by default. Every connection have to be authenticated. Access rights and id verification have to be confirmed repeatedly, irrespective of the place the request comes from. Instead of simply managing roles and permissions, Zero Trust requires each try to be authenticated and segmented to scale back motion inside the system. This strategy considerably limits the danger of unauthorized entry and potential breaches.
2. Leverage the Power of AI for Active Monitoring
As safety demand will increase, so does the necessity to monitor cloud environments. Traditional means could be enhanced with AI-powered instruments, like real-time menace detection, anomaly identification, predictive evaluation, and automatic responses. AWS CloudPath could be merged with AI-powered platforms to supply insights, flag harmful behaviour, and scale back alert overload. Maintaining AI-driven monitoring permits for proactively managing vulnerabilities, misconfigurations, and breaches earlier than they grow to be an issue.
3. Integrate IaC
With Infrastructure as Code (IaC), you possibly can outline and handle your parts in the cloud, considerably lowering human error. Infrastructure as code automates the method of configuring, deploying, and sustaining infrastructure, guaranteeing consistency throughout your cloud surroundings. IaC instruments similar to Terraform and AWS CloudFormation implement safe configurations and assist your online business scale extra effectively.
4. Use a CASB for Visibility and Control.
By serving as a safety boundary between customers and cloud functions, Cloud Access Security Brokers (CASB) present one other layer of safety. They supply intensive cloud utilization visibility, detect shadowed IT, and implement real-time information safety insurance policies. CASB moreover helps organizations with compliance, supervising consumer exercise, and lowering the dangers related to information leakage by means of extreme file sharing or suspicious login exercise. For new companies utilizing varied cloud providers, a CASB allows uniform coverage enforcement throughout gadgets.
Helpful Tools & Resources for Startups
Here are some instruments that may provide help to get began. The better part is that accessing a few of these sources is freed from cost.
1. AWS Well-Architected Tool.
With this software from Amazon Web Services, you possibly can examine whether or not your cloud setup is perfect. It advises you on how to right frequent points and may enhance your safety, efficiency, and price. Please be aware that making use of suggestions from this software incurs fees
2. CIS Benchmarks
CIS Benchmarks are trusted pointers developed by safety consultants to assist safe varied techniques (e.g, Windows, Linux, Cloud, and so on.). Download them totally free and comply with the steps to harden your setup.
3. ScoutSuite, Prowler, CloudSploit.
These are open-source instruments that scan your cloud surroundings for weak spots. They’re helpful in discovering misconfigurations that hackers can exploit.
4. Compliance Checklists (SOC 2, ISO 27001, GDPR).
If you battle to meet safety requirements or authorized necessities, these checklists will provide help to alongside the way in which. They define the steps you will need to take to keep compliant and safe buyer information.
Staying Secure from the Start
When utilizing cloud providers, you want to perceive your accountability. Although cloud suppliers handle lots, your staff is chargeable for important areas like software safety, consumer entry, and information safety.
Security must be a part of your basis; it should not be an afterthought. Being ready from the beginning helps you keep away from expensive errors and achieve clients’ belief.
Take a second to evaluation your present cloud obligations. Are you overlaying all of your bases?
The submit The Shared Responsibility Model: What Startups Need to Know About Cloud Security in 2025 appeared first on Datafloq.